So what does, “We need a more secure mobile infrastructure” mean? Over the next few weeks, we’ll be writing a series of posts that will address specific needs for a more secure consumer-facing mobile infrastructure. We’ll start first by talking about how securing consumer-facing mobile is different than current enterprise mobility solutions.
Consumer-facing mobile security is different
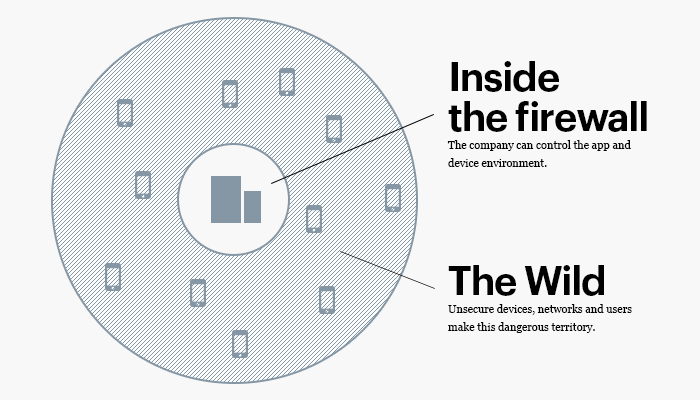
There has been a significant investment in securing enterprise mobility — mobile apps that are developed for internal business use, or the actions an enterprise takes to protect data and communication on devices that are used for internal business purposes. In these situations, the enterprise has control and insight into both the app AND the device. This control allows them to enforce certain policies, and take a variety of measures to guard against external attack vectors. This is a relatively well-established part of the security industry with some pretty big players.
The devices and apps that are used for internal business purposes operate in an ecosystem in which the enterprise can exert significant levels of control. These are relatively smaller ecosystems limited to the apps and devices that are being used by a company’s employees. Policies that secure internal mobile initiatives are generally based around the following:
- Measures to secure the device
- Measures to secure the app
- Policies to ensure appropriate user behavior
The moment we consider consumer-facing mobile — mobile apps or purposed-devices meant to engage customers as opposed to internal employees — the ecosystem to secure grows exponentially. Now, we have to consider the device of EVERY customer that will have access to the app. Once a business puts an app in a store like the AppStore or Google Play, the app is, in every describable way, in the wild.
The business no longer has the ability to take measures to secure the device, nor can it exert control over the user (at least if the business want its app to have any traction). The business is now completely reliant on its ability to continually secure the app. A variety of risk factors that are posed by device integrity and user behavior are now introduced.
It’s those factors, and the specific challenges that they pose, that need to be addressed.
More to come.