Google has deprecated three settings options (Ensure Verify Apps Enabled, Debugging Features Allowed, and Safe Boot Disabled) and replaced them with two new options (Google Play Protect Verify Apps and Developer Settings):
Before resaving any existing Policies
please be sure the new Google Play Protect Verify Apps and Developer Settings are configured as desired
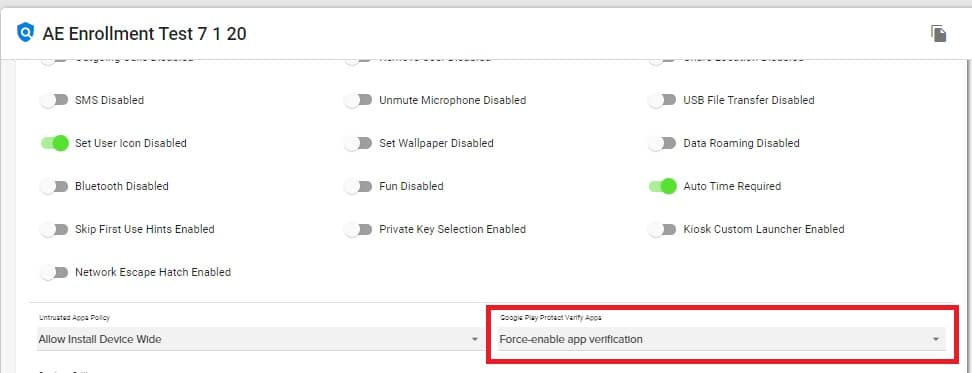
The Ensure Verify Apps Enabled setting has been replaced by the new Google Play Protect Verify Apps setting.
- The new Google Play Protect Verify Apps setting is located in the Policy=>General Settings, near the bottom.
- Rather than simply toggling on or off the Ensure Verify Apps Enabled setting, the new Google Play Protect Verify Apps setting offers the following options:
- Force-enable app verification – Play Protect App Verification will be turned on
- Allow user to choose enable app verification – User will be able to choose to turn on or off Play Protect App Verification
- Unspecified – The Policy will not make any adjustments to the device setting
- If a Policy previously had Ensure Verify Apps Enabled toggled ON, it has been updated to the “Force-enable app verification” settings option for the new Google Play Protect Verify Apps setting.
- If a Policy previously had Ensure Verify Apps Enabled toggled OFF, it has been updated to “Allow user to choose enable app verification” setting option for the new Google Play Protect Verify Apps setting.
- The new Google Play Protect Verify Apps setting is located in the Policy=>General Settings, near the bottom.
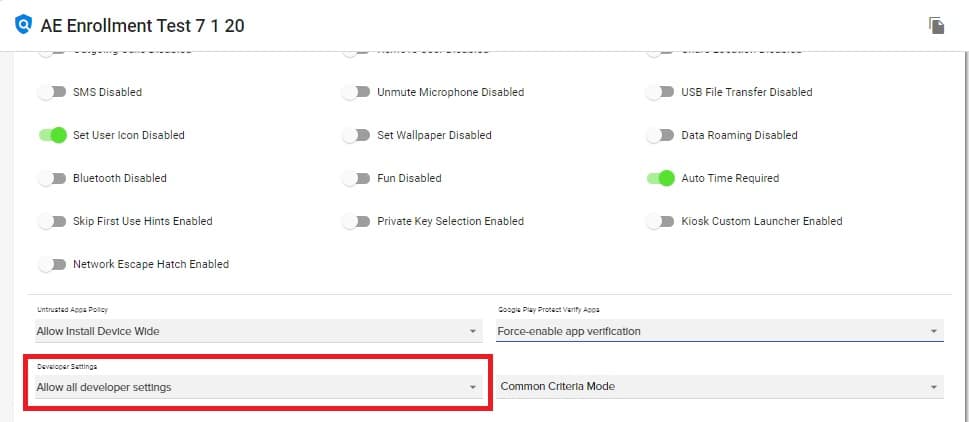
The Debugging Features Allowed and the Safe Boot Disabled settings have been replaced by the new Developer Settings option.
- The new Developer Settings option is located in the Policy=>General Settings, near the bottom.
- The new Developer Settings option offers the following options:
- Disable all developer settings – Safe Boot and Debugging Features will both be disabled, and will not be able to be enabled by a user on the device.
- Allow all developer settings – Safe Boot and Debugging Features will be allowed on the device, but a user can toggle Developer options off on the device
- Unspecified – The Policy will not make any adjustments to the device setting
- The new Developer Settings option is located in the Policy=>General Settings, near the bottom.
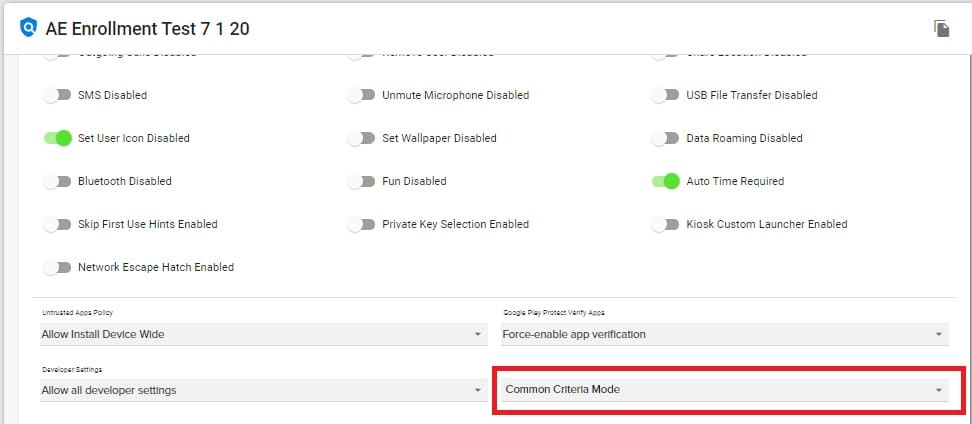
A new Common Criteria Mode Policy setting option has been added
Common Criteria Mode offers a new Policy setting option
- The new Common Criteria Mode setting is located in the Policy=>General Settings, near the bottom.
- The new Common Criteria Mode setting offers the following options:
- Enable – Enable Common Criteria Mode
- Disable – Disable Common Criteria Mode
- Unspecified – The Policy will not make any adjustments to the device setting
- Common Criteria Mode controls security standards defined in the Common Criteria for Information Technology Security Evaluation. Enabling Common Criteria Mode increases certain security components on a device, including AES-GCM encryption of Bluetooth Long Term Keys, and Wi-Fi configuration stores.
- The new Common Criteria Mode setting is located in the Policy=>General Settings, near the bottom.
WARNING:
Common Criteria Mode enforces a strict security model typically only required for IT products used in national security systems and other highly sensitive organizations. Standard device use may be affected. Only enable if required.